
Safety related
Details >>This book introduces the basic knowledge, security technology and application practice of computer network security. It mainly introduces the basic knowledge of network security, security risks and threats, OSI security architecture, etc., and various security technologies involved in network security, such as cryptography, firewall, security authentication, EFS, IPSec, hacker attack and prevention, vulnerability scanning, network monitoring, intrusion detection, virus prevention and other related knowledge.
To ensure network security and carry out network security construction, the first step is to comprehensively understand the system, evaluate the system security, and recognize their own risks, so as to quickly and accurately solve Intranet security problems.
-

How do I close all pop-ups on my computer? One move to turn off all ads including 360 Security Guard pop-ups
There are all kinds of advertisements on computers all the time. How can we ban the display of advertisements? Today we share a trick to turn off all advertising pop-ups, including all advertising Windows that 360 Security Guards pop up... The 24-05-09 -

Computer 360ai office How to close? 360 security guard ai office closing method
The ai icon always appears in the lower right corner of the computer, and 360ai office will appear after the delay. If you want to turn off the ai office icon, how to operate it? Below we have summarized a variety of solutions, please see the details below... The 24-05-09 -

How to close 360AI big members pop-up window advertising tips? 360 security guard ai big member remind closing method
360 security guards always pop up the promotion advertisement of ai big members, want to close this pop-up window, how to operate? We click on the 360 Setup center, click on the pop-up window setting, the pop-up window setting is pulled down, and turn off the AI member reminder... The 24-05-09 -

How to add ip segment to Tinder ip Blacklist? How to use tinder ip blacklist function
When using the computer, there are users who want to restrict the specified IP access, so how to turn on this function and add IP blacklist in Tinder Security Center? The following is about how to use Tinder security software to add ip blacklist specific operation methods... The 24-02-20 -

MD5, SHA1, and SHA256 file hash check method shared
File hash operation refers to the specific algorithm to convert the file content into a fixed length hash value, which is used to seriously whether the file we download from the Internet is consistent with the official, because in many cases the official is easy to be maliciously modified. The 24-02-08 -

Professional file MD5, SHA-256/512 algorithm support verification tool (file hash check set)
The following to recommend a few easy to use free sha1, SHA-256 verification tool software, the file downloaded online do not know whether it has been modified, then you need such a tool, need the small partners to understand... The 24-02-08 -

360 Security guard how to open not participate in the user experience improvement plan?
360 Security guard how to open not participate in the user experience improvement plan? The computer installed 360 anti-virus software, the software will automatically check to participate in 360 user experience improvement plan, but there are many small partners worried about their privacy data is abused, do not want to participate, here we come... The 23-10-09 -

Kaspersky desktop icon does not display what to do? Kaspersky tips for adding desktop ICONS
Kaspersky desktop icon does not display what to do? After downloading and installing Kaspersky software on my computer, I find that the software icon is not displayed on my desktop. What should I do? Let's take a look at Kaspersky's tips for adding desktop ICONS... The 23-08-07 -
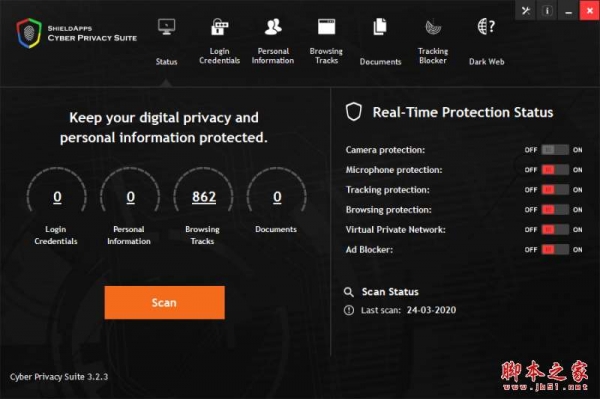
How to activate Cyber Privacy Suite for free with activation tutorial/hack patch
Cyber Privacy Suite activation tutorial + crack patch sharing, Cyber Privacy Suite is a super powerful network privacy protection software, it provides protection of our computer network security functions, so that we will not be malicious tracking when browsing the web. The 23-05-16 -
360 Disconnect First Aid Kit How to repair network connection configuration? 360 disconnect First aid kit repair network connection configuration tutorial
This article mainly introduces how to repair the network connection configuration of the 360 disconnected first aid kit. 360 network first aid kit repair network connection configuration tutorial related information, need friends can refer to the details of this article... The 23-05-06 -

Lenovo Computer Manager how to restore backup drivers? Lenovo computer manager restore backup driver tutorial
This article mainly introduces Lenovo computer manager how to restore the backup driver? Lenovo computer manager restore backup driver tutorial related information, need friends can refer to the details of this article... The 23-04-27 -
Lenovo Computer Manager How to enable Lenovo lock screen? Lenovo computer manager enables Lenovo lock screen tutorial
This article mainly introduces how Lenovo computer manager enables Lenovo lock screen? Lenovo computer butler enable Lenovo lock screen tutorial related information, need friends can refer to the details of this article... The 23-04-27 -

How does Lenovo Computer Manager retrieve quarantined files? Lenovo computer Manager retrieve quarantined files tutorial
This article mainly introduces the Lenovo computer manager how to retrieve the quarantined files? Lenovo computer manager to retrieve the relevant information of the isolated file tutorial, the need of friends can refer to the details of this article... The 23-04-27 -

Where does Lenovo computer Butler manage boot items? Lenovo computer butler manages boot item teaching
This article mainly introduces the Lenovo computer butler where to manage the boot item? Lenovo computer butler management boot item teaching related information, need friends can refer to the details of this article... The 23-04-27 -

Tinder Security Software How to turn off Self-starting Tinder Security Software turn off self-starting tutorial
Some people want to know how to turn off Tinder security software to start. Here is a way for you to close the tinder security software to start, you can understand the need... The 23-04-25 -

How to set Tinder mask specified IP? Tinder Secure directional interception of computer inbound IP address skills
How to set Tinder mask specified IP? Tinder security can set directional interception, how to operate? Let's take a look at Tinder's safe directional interception of computer inbound IP address skills... The 23-04-25 -

How to activate Secret Disk Pro for free with activation tutorial + Patch
Secret Disk Pro Activation tutorial + Activation patch share! Secret Disk Professional is a powerful professional hard disk encryption software that helps users encrypt all kinds of important data easily, ensuring privacy and information security. Secret Dis... The 23-04-15 -

360 Security Guard deletes unexecutable recovery steps of SqlServer jobs by mistake (360 indicates that the sql server high-risk plan task is
Today, the server uses 360 to monitor sqlserver high-risk plan tasks. After deleting the sqlserver database job, it is found that the SQL automatic backup task fails due to sudden loss. The following gives the specific solution. The 23-03-23

